Article 1:Why is face attendance better than fingerprint?
Practically 100% accuracy: Time and again it has been proven that fingerprint systems fail when fingers are dirty, oily, wet or bruised. Workers who work in oiling systems can’t register their attendance with faded fingerprints. Cuts on fingers return errors. It is often frustrating to try attendance multiple times.
That is not the case with face recognition attendance. It has been tried, tested and proven that it is practically 100% accurate. Employees simply walk towards it and attendance is captured. It works even when hairstyles change wear glasses, or employees age.
Touchless safety: With covid-19, the world has become increasingly aware of the risks of contact-based attendance systems. There is no attendance system, other than face id attendance system which is absolutely touchfree. The user has to simply show his face. The system is triggered automatically.
Even after the world is covid-free, people will be conscious of the touches they make and it will be good to provide a hygienic system.
Wow experience: With attendance time cut-down to less than a second and no action required from the user-end, face id attendance is by far the best biometric system. It wows employees who don’t require training and are happy to adopt immediately. Think about it when you are holding a cup of coffee in one hand and your handbag in the other when you have to do fingerprint attendance. What if we change to face recognition attendance. Save your trouble by making it much easier than just standing in front of the screen.

Article 2:How does face recognition attendance system work?
It stores user faces in the database of the device with a different size of screen, in TOMMI cases, from 4.3inch to 13inch. When an employee stands in front of the screen, it captures the face and make a realtime comparison with the stored face image. If it matches, clock-in or clock-out attendance is recorded in the device. It can do liveness judegement against photo or video deceit.

Article 3:How does face attendance win over other biometric systems?
Many companies have been using fingerprint time attendance system, which may be a good substitute to card punching system. Neither of them is perfect in terms of reliability and security. Face recognition time attendance devices have been used by more and more large companies in recent years. Yet many medium and small-sized organizations are still working with older technologies.
Shall we upgrade to face ID attendance systems? We’d better do an objective analysis.

Article 4:What are the benefits of Access Control facial recognition?
One of the fastest growing trends in building design and technology is the application of touch-free user experiences. The combination of rapid expansion in multi-tenant living & working spaces and the Coronavirus pandemic has resulted in an increasing requirement for contactless living and working environments.
· Improved security
The latest generation of Facial Recognition devices provides accurate and highly secure authentication, when compared with traditional access methods such as PIN code or keyfob door entry.
· Fast, convenient and remote management of user IDs
Addition, removal and control of User accounts is easy and simple for system administrators and can be fully managed remotely.
Whereas authentication via physical device requires fobs or cards to be handed-out in person or delivered (and returned), new User IDs can be created and disabled by system administrators (such as security, HR or concierge personnel) from any remote site using cloud-based management platforms, significantly speeding-up the process to save time and money.
· No authentication device required
Many door entry and access identification methods require the use of a physical device to authenticate – such as keyfob, RFID card or smartphone. Should the user forget or lose their ‘device’ (or worse still – have it stolen), then they will be unable to access the building.
The authenticating ‘device’ of face recognition will always, of course, be with you!
· Integration with other platforms
Facial recognition access control systems can also be integrated with other logistical and system platforms, such as time & attendance, automatic payment systems or building management systems, helping to develop smart building environments.
Article 5:How will facial recognition systems & algorithms work in 2022?

The facial recognition technology market is growing rapidly. From airports relying on biometric data to screen international passengers, law enforcement depending on it to catch criminals, and social media using it to authenticate the user, facial recognition technology is the need of the hour.
In 2022, the facial recognition market is expected to reach $7.7 billion, up from $4 billion in 2017. This is because facial recognition has a wide range of commercial applications. It can be used for a variety of purposes, including surveillance and marketing.
How do humans recognize a face?
Recognition systems in our brains are complex. In fact, scientists are still trying to figure it out. What we can assume is that the neurons in our brain first identify the face in the scene (from the person’s body to its background), we extract the facial features, and store it in our own kind of database. Using our memory as a database, we can then classify the person according to their features. We have been trained on an infinitely large dataset and infinitely extensive neural network.
Facial Recognition software in machines is implemented the same way. First, we apply a facial detection algorithm to detect faces in the scene, extract facial features from the detected faces, and use an algorithm to classify the person.
How does the workflow of a Facial Recognition System work?
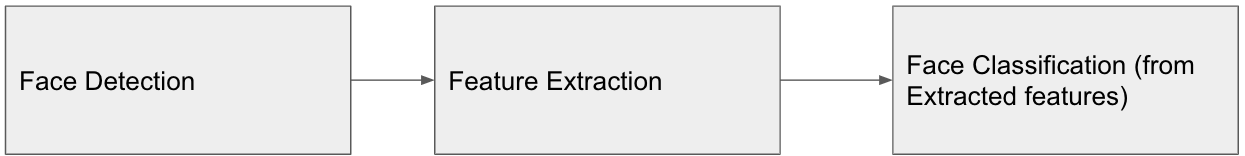
1Face detection
Face detection is a specialized version of Object Detection, where there is only one object to detect – Human Face.
Just like computational time and space trade-offs in Computer Science, there’s a trade-off between inference speed and accuracy in Machine Learning algorithms as well. There are many object detection algorithms out there, and different algorithms have their speed and accuracy trade-offs.
We evaluated different state-of-the-art object detection algorithms:
OpenCV (Haar-Cascade)
MTCNN
YoloV3 and Yolo-Tiny
SSD
BlazeFace
ShuffleNet and Faceboxes
To build a robust face detection system, we need an accurate and fast algorithm to run on a GPU as well as a mobile device in real-time.
Accuracy
In real-time inference on streaming video, people can have different poses, occlusions, and lighting effects on their face. It is important to precisely detect faces in various lighting conditions as well as poses.

Detecting faces in various poses and lighting conditions
OpenCV (Haar-Cascade)
We started with Haar-cascade implementation of OpenCV, which is an open-source image manipulation library in C.
Pros: Since this library is written in C language. It is very fast for inference in real-time systems.
Cons: The problem with this implementation was that it was unable to detect side faces and performed poorly in different poses and lighting conditions.
MTCNN
This algorithm is based on Deep Learning methods. It uses Deep Cascaded Convolutional Neural Networks for detecting faces.
Pros: It had better accuracy than the OpenCV Haar-Cascade method
Cons: Higher run time
YOLOV3
YOLO face detection (You look only once) is the state-of-the-art Deep Learning algorithm for object detection. It has many convolutional neural networks, forming a Deep CNN model. (Deep means the model architecture complexity is enormous).
The original Yolo model can detect 80 different object classes with high accuracy. We used this Yolo facial recognition model for detecting only one object – the face.
We trained this algorithm on WiderFace (image dataset containing 393,703 face labels) dataset.
There is also a miniature version of the Yolo algorithm for face detection available, Yolo-Tiny. Yolo-Tiny takes less computation time by compromising its accuracy. We trained a Yolo-Tiny model with the same dataset, but the boundary box results were not consistent.
Pros: Very accurate, without any flaw. Faster than MTCNN.
Cons: Since it has colossal Deep Neural Network layers, it needs more computational resources. Thus, it is slow to run on the CPU or mobile devices. On GPU, it takes more VRAM because of its large architecture.
SSD
SSD (Single Shot Detector) is also a deep convolutional neural network model like YOLO.
Pros: Good accuracy. It can detect in various poses, illumination, and occlusions. Good inference speed.
Cons: Inferior to YOLO model. Though inference speed was good it was still not adequate to run on CPU, low-end GPU, or mobile devices.
BlazeFace
Like its name, it is a blazingly fast face-detection algorithm released by Google. It accepts 128×128 dimension image input. Its inference time is in sub-milliseconds. This algorithm is optimized to be used in face recognition on mobile phones. The reasons it is so fast are:
It is a specialized face detector model, unlike YOLO and SSD, which were originally created to detect a large number of classes. Thus BlazeFace has a smaller Deep Convolutional Neural Network architecture than YOLO and SSD.
It uses Depthwise Separable Convolution instead of standard Convolution layers, which leads to fewer computations.
Pros: Very Good inference speed and accurate face detection.
Cons: This model is optimized for detecting facial images from a mobile phone camera, and thus it expects that face should cover most of the area in the image. It doesn’t work well when the face size is small. So in the case of CCTV camera images, it doesn’t perform well.
Faceboxes
The latest face recognition algorithm we used is Faceboxes. Like BlazeFace, it is a Deep Convolutional Neural network with small architecture and designed just for one class – Human Face. Its inference time is real-time fast on CPU. Its accuracy is comparable to Yolo for face detection. It can detect small and large faces in an image precisely.
Pros: Fast inference speed and good accuracy.
Cons: Evaluation is in progress.
2Feature extraction
After detecting faces in an image, we crop the faces and feed them to a Feature Extraction Algorithm, which creates face embedding- a multi-dimensional (mostly 128 or 512 dimensional) vector representing features of the face.
We used the FaceNet algorithm to create face-embeddings.
The embedding vectors represent the facial features of a person’s face. So embedding vectors of two different images of the same person will be closer and that of a different person will be farther. The distance between two vectors is calculated using Euclidean Distance.
3
Face classification
After getting the face-embedding vectors, we trained a classification algorithm, K-nearest neighbor (KNN), to classify the person from his embedding vector.
Suppose in an organization there are 1000 employees. We create face-embeddings of all the employees and use the embedding vectors to train a classification algorithm that accepts face-embedding vectors as input and returns the person’s name.
A user could apply a filter that modifies specific pixels in an image before putting it on the web. These changes are imperceptible to the human eye but are very confusing for facial recognition algorithms – ThalesGroup
https://www.engati.com/blog/facial-recognition-systems By Aniket Maurya
Article 6:What are the applications of the Facial Recognition System?

Airports
People entering and exiting airports can be tracked using facial recognition systems. The technology has been used by the Department of Homeland Security to identify people who have overstayed their visas or are under criminal investigation.
Mobile phone companies
Face recognition was first used by Apple to unlock its iPhone X, and the technology was carried over to the iPhone XS. Face ID verifies that you are who you say you are when you access your phone. According to Apple, the odds of a random face unlocking your phone are one in a million.
Colleges & universities
In fact, facial recognition software can play a role. Your professor might find out if you skip class. Don’t even consider having your bright roommate take your exam.
Social media
When you upload a photo to Facebook, it uses an algorithm to detect faces. If you want to tag people in your photos, the social media company will ask you. It can link to their profiles and recognize faces with an accuracy of 98%.
Marketing and advertisement campaigns
When marketing a product or an idea, marketers frequently consider factors such as gender, age, and ethnicity. Even at a concert, facial recognition can be used to identify specific audiences.
New tech brings new opportunities
Advancements in facial recognition systems and computer vision have taken great leaps. But this is only the beginning of the technological revolution. Imagine how powerful the duo of face recognition algorithms and chatbot technology would be!
It’s never too late to become a part of this movement.
By Aniket Maury
Article 7:Touch-free Access Control
Facial recognition is one of a number of touch-free authentication methods being adopted for both access control and door intercom systems, as part of contactless pathway parameters in latest-generation building design.
The Coronavirus pandemic has resulted in a huge growth in the requirement and application of touch-free technologies and products in workplace and multi-tenant environments to reduce the frequency of contact between individuals, thereby helping to reduce the risk of virus transmission.
Therefore, authentication methods which allow users to identify themselves without physically touching devices (technologies such as RFID, NFC, Bluetooth – and now face recognition, of course) are becoming the preferred options for door intercom and access control systems.
Can face recognition be fooled by photographs?
The latest AI face recognition access control systems – such as the Tommi devices – also incorporate anti-spoofing ‘liveness’ detection, using an additional built-in camera to detect 3-dimensional facial awareness and movement.
Article 8:What are the benefits of Access Control facial recognition?
Hands-free user authentication
One of the fastest growing trends in building design and technology is the application of touch-free user experiences. The combination of rapid expansion in multi-tenant living & working spaces and the Coronavirus pandemic has resulted in an increasing requirement for contactless living and working environments. Improved security
Improved security
The latest generation of Facial Recognition devices provides accurate and highly secure authentication, when compared with traditional access methods such as PIN code or keyfob door entry.
Fast, convenient and remote management of user IDs Addition, removal and control of User accounts is easy and simple for system administrators and can be fully managed remotely.
Whereas authentication via physical device requires fobs or cards to be handed-out in person or delivered (and returned), new User IDs can be created and disabled by system administrators (such as security, HR or concierge personnel) from any remote site using cloud-based management platforms, significantly speeding-up the process to save time and money.
No authentication device required
Many door entry and access identification methods require the use of a physical device to authenticate – such as keyfob, RFID card or smartphone. Should the user forget or lose their ‘device’ (or worse still – have it stolen), then they will be unable to access the building.
The authenticating ‘device’ of face recognition will always, of course, be with you!
Integration with other platforms
Facial recognition access control systems can also be integrated with other logistical and system platforms, such as time & attendance, automatic payment systems or building management systems, helping to develop smart building environments.
Article 9: Facial Recognition vs. Palm Vein Biometrics ---5 Important Differences
Facial recognition and palm vein are two of the leading biometrics on the market today, but they are polar opposites in many ways.
How do they work?
Facial recognition technology works by mapping the unique geometry of a person’s face, such as the distance from the chin to the forehead, distance between the eyes, length of the jawline, etc.
Palm vein technology works by using infrared light to map the unique vein pattern of a person’s palm, measuring over 5 million data points in their vein structure.
With both biometrics, this information then gets converted into an encrypted code that becomes the person’s unique biometric ID. When they scan their face or palm, their biometric code is checked against existing codes in the system, and if it matches up, they are identified.
But while the end result — identification — might be the same, the way these two biometrics achieve this is dramatically different. This has several important consequences.
These are the five key differences between facial recognition and palm vein that you should know about before choosing one for your business.
1. Privacy
The biggest difference between facial recognition and palm vein biometrics is in the area of privacy.
Facial recognition has received widespread criticism in the last few years due to the privacy concerns it creates.
Because your face is exposed everywhere you go, face recognition cameras can easily identify you from a distance, making it possible for you to be tracked in public and creating serious privacy risks.
Palm vein, on the other hand, is privacy-by-design. Because your palm vein pattern is concealed inside your hand, it requires a combination of infrared light and a close-up ultra-HD camera to capture it.
So, unlike with face recognition, it is impossible for your palm vein pattern to be captured from a distance. To be identified, you have to deliberately scan your palm over the palm vein scanner — it cannot be captured without your consent.
This is what makes palm vein a consent-based biometric, giving it clear advantages over facial recognition in terms of privacy.
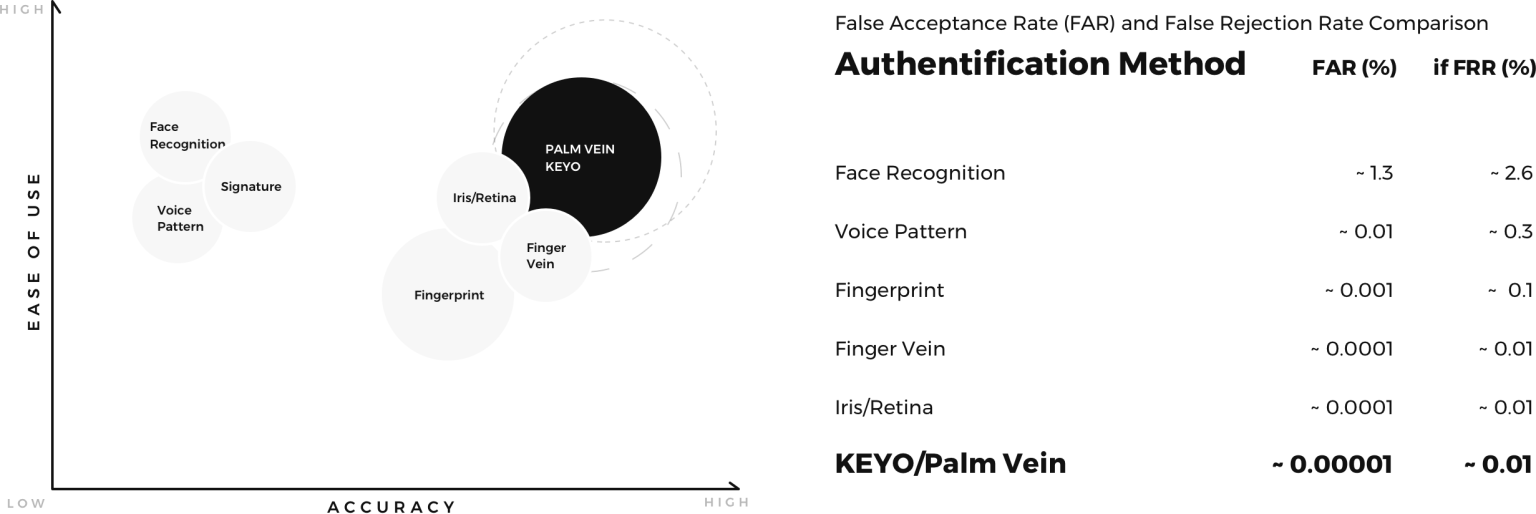
2. Accuracy
Aside from privacy, accuracy is the second biggest difference between facial recognition and palm vein.
The accuracy of a biometric is measured by two factors: False Rejection Rate (FRR), and False Acceptance Rate (FAR). The lower the number, the more accurate the biometric is.
The FRR measures the chance an authorized user will be incorrectly denied access, whereas the FAR measures the chance an unauthorized user will be incorrectly allowed access.
Facial recognition has the highest FAR and FRR of any biometric on the market. On the contrary, palm vein has the lowest — making it 260 times more accurate in terms of FRR, and 130 thousand times more accurate in terms of FAR.
Additionally, facial recognition has an additional flaw: it’s not equally accurate for all people. Face recognition algorithms have been proven to be less accurate on women and people of color.
Any identification technology should be equally accurate for all people, because the dangers of inaccurate identification are too high. Inaccurate identification makes it possible for you to be misidentified as someone else, which has potentially dire consequences (particularly when used by law enforcement).
It’s also just plain inconvenient. Being misidentified and incorrectly denied access to something that’s yours is extremely annoying, and it defeats one of the core benefits of biometrics in the first place: convenience.
So in terms of accuracy, facial recognition performs worse than virtually any other biometric, making palm vein the clear winner.
3. Security
Facial recognition’s privacy risks and reduced accuracy also have a third consequence: reduced security.
The reduced accuracy of face recognition makes it more likely to misidentify users, potentially allowing access to unauthorized personnel and creating security risks.
But the biggest security risk of facial recognition is its vulnerability to spoofing. Since your face is exposed everywhere you go, it’s much easier for hackers to forge a 3D image of your face to fool a facial recognition device.
With palm vein, since your vein pattern is concealed inside your hand, it can only be captured when you deliberately scan your palm. Otherwise, it’s completely hidden, making it nearly impossible for a thief to forge or steal it.
These two features of palm vein — the increased accuracy and the fact that it’s internal — make it generally a much more secure biometric than facial recognition.
4. Convenience
There is one key advantage that facial recognition has over all other biometrics: convenience.
Despite the security and privacy risks associated with it, the fact that face recognition technology can automatically identify a user from a distance makes it very convenient if the user consents to this.
For example, face recognition on modern smartphones (such as Apple’s Face ID feature) allows users to unlock their phone just by looking at it. How convenient!
Additionally, the privacy risks of facial recognition don’t apply to smartphones because the user’s biometric data is stored directly on the device, rather than in a database, so it can’t be used for surveillance purposes.
This makes facial recognition a seamless, convenient choice for unlocking smartphones. However, when used on public surveillance systems instead of personal devices, the privacy risks of facial recognition greatly outweigh the convenience benefits.
Palm vein, on the other hand, doesn’t have the long-range automatic identification capabilities that facial recognition has, since it requires a close-up (but contactless) scan of the palm to identify the user. So while this gives it important privacy and security benefits, it could potentially be seen as a drawback in terms of convenience.
Additionally, because palm vein is newer and less familiar, it arguably has a bigger learning curve than older biometrics (such as fingerprint), or highly intuitive biometrics (such as facial recognition, where you don’t actually have to do anything to be identified).
However, the simple, ergonomic motion of palm vein means that it’s still an easy-to-use and user-friendly biometric. Nonetheless, facial recognition, especially on personal devices, does have significant convenience benefits that palm vein doesn’t.
This makes palm vein ideal when shared among large numbers of people (e.g., employees and customers), while facial recognition is ideal for individual use on personal devices (e.g., smartphones and tablets).
5. Legal Compliance
In recent years, major privacy regulations have been popping up around the globe. Since the creation of the GDPR in 2016, many major economies have created their own GDPR copycat laws, making privacy regulations a worldwide trend.
Because of this, companies today have more restrictions than ever on data collection.
And the number-one factor in privacy regulations around the world is consent. Companies must obtain explicit user consent before they’re allowed to capture user data, or they face significant legal risks.
Because of this, the importance of privacy-friendly technologies is more important than ever. Companies that implement such technologies have much less legal risk to worry about, and much less hassle to deal with.
Since facial recognition allows for the possibility of capturing a person’s data without their consent, it is critical for companies to put safeguards in place to ensure that they’ve obtained explicit, verifiable consent before collecting user data — or they risk facing serious fines.
The benefit palm vein has over facial recognition is that, since it has consent automatically built-in, it has far less legal risk associated with it.
With palm vein, there’s no question whether a user consented to give their biometric data or not, because it can’t be captured without a person’s explicit interaction with the terminal.
And because automatic, forced capturing of biometric data isn’t possible with palm vein (as it is with facial recognition), it is automatically in-line with the consent-focused guidelines in most data protection regulations.
This makes palm vein the more convenient, less risky, hassle-free choice for companies looking to implement biometrics in their business.
Conclusion
Facial recognition and palm vein are powerful biometric technologies with a large range of applications, but they are complete opposites in many ways.
For public and business use, palm vein has many advantages over facial recognition, offering various privacy, security, and accuracy benefits that facial recognition doesn’t have.
Additionally, in terms of trustworthiness and legal risk, palm vein is generally the less risky option for companies looking to implement biometrics in their business because of its privacy-focused design.
For use on personal devices, however, facial recognition is a convenient and easy-to-use authentication method that doesn’t have the same privacy risks as the kind of facial recognition that is used in surveillance cameras.
These factors make palm vein ideal biometric for shared use (e.g., used by customers or employees), whereas facial recognition is a great choice for authenticating personal devices.
Every biometric has its unique pros and cons. To learn more about the other types of biometrics on the market and help determine which one is right for your business, check out our ebook exploring all of the different biometrics on the market.
Article 10:The sense behind the biometric measures




Thanks for your blog, nice to read. Do not stop.